1. Open a command prompt.
2. Type netstat -o -n -a | findstr 127.0.0.1:8008
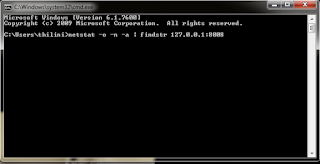 3. Find the last column in the displayed result. It is the PID of the process which listening to port 8008.
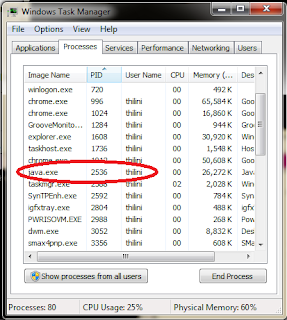
3. Find the last column in the displayed result. It is the PID of the process which listening to port 8008.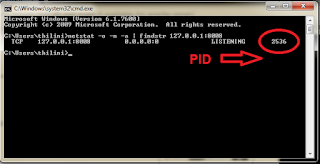 4. Open task manager and inside process tab find PID column. If you cannot see PID column, go to view>select columns and check PID check-box.
4. Open task manager and inside process tab find PID column. If you cannot see PID column, go to view>select columns and check PID check-box.5. Arrange processes by PID then find the PID resulted previously and see the corresponding process.
NETSTAT
The NETSTAT command will show you whatever ports are open or in use, but it is NOT a port scanning tool! If you want to have your computer scanned for open ports see this page instead (link will follow shortly).
Open Command Prompt and type:
C:'WINDOWS>netstat -an |find /i "listening" TCP 0.0.0.0:135 0.0.0.0:0 LISTENING TCP 0.0.0.0:445 0.0.0.0:0 LISTENING TCP 0.0.0.0:1025 0.0.0.0:0 LISTENING TCP 0.0.0.0:1084 0.0.0.0:0 LISTENING TCP 0.0.0.0:2094 0.0.0.0:0 LISTENING TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING TCP 0.0.0.0:5000 0.0.0.0:0 LISTENING
You can redirect it to a text file by adding >c:'openports.txt to the command, if you want to:
netstat -an |find /i "listening" > c:'openports.txt
netstat -an |find /i "listening" > c:'openports.txt
You can also change "listening" to "established" to see what ports your computer actually communicates with:
C:'WINDOWS>netstat -an |find /i "established"
TCP 192.168.0.100:1084 192.168.0.200:1026 ESTABLISHED
TCP 192.168.0.100:2094 192.168.0.200:1166 ESTABLISHED
TCP 192.168.0.100:2305 209.211.250.3:80 ESTABLISHED
TCP 192.168.0.100:2316 212.179.112.230:80 ESTABLISHED
TCP 192.168.0.100:2340 209.211.250.3:110 ESTABLISHED
Note: In Windows XP and Windows Server 2003, you can type NETSTAT -O to get a list of all the owning process ID associated with each connection:
C:'WINDOWS>netstat -ao |find /i "listening" TCP pro1:epmap pro1.dpetri.net:0 LISTENING 860 TCP pro1:microsoft-ds pro1.dpetri.net:0 LISTENING 4 TCP pro1:1025 pro1.dpetri.net:0 LISTENING 908 TCP pro1:1084 pro1.dpetri.net:0 LISTENING 596 TCP pro1:2094 pro1.dpetri.net:0 LISTENING 596 TCP pro1:3389 pro1.dpetri.net:0 LISTENING 908 TCP pro1:5000 pro1.dpetri.net:0 LISTENING 1068
You can use PULIST from the W2K Resource Kit (Download Free Windows 2000 Resource Kit Tools) to find the PID and see what process uses it and who started it. For example, you found out that your computer had an open connection to a remote IP address on TCP port 80, and you don't have any Internet Explorer or other browser windows open. You want to find out what process is using that session.
C:'WINDOWS>netstat -no Active Connections Proto Local Address Foreign Address State PID TCP 192.168.0.100:2496 212.179.4.7:80 ESTABLISHED 1536
You can then use PULIST with the FIND command:
C:'WINDOWS>pulist |find /i "1536" Process PID User LUCOMS~1.EXE 1536 DPETRI'danielp
In this case, LUCOMS~1.EXE is run by DANIELP (myself) and as it happens, it's the Symantec Live Update process.
You can also look in Task Manager for the respective PID.
- To set up Task Manager to show the PID column open Task Manager by using CTRL+SHIFT+ESC.
- Go to the Processes tab, click View and then Select Columns.
- In the Select Columns windows click to select PID and then click Ok.
- You can sort the PID column to display the PIDs in descending or ascending order.
To see all open, established, closing and other used ports type:
C:'WINDOWS>netstat -a Active Connections Proto Local Address Foreign Address State TCP pro1:epmap pro1.dpetri.net:0 LISTENING TCP pro1:microsoft-ds pro1.dpetri.net:0 LISTENING TCP pro1:1025 pro1.dpetri.net:0 LISTENING TCP pro1:1084 pro1.dpetri.net:0 LISTENING TCP pro1:2094 pro1.dpetri.net:0 LISTENING TCP pro1:3389 pro1.dpetri.net:0 LISTENING TCP pro1:5000 pro1.dpetri.net:0 LISTENING TCP pro1:1084 srv1.dpetri.net:1026 ESTABLISHED TCP pro1:2094 srv1.dpetri.net:1166 ESTABLISHED TCP pro1:2365 srv1.dpetri.net:epmap TIME_WAIT TCP pro1:2366 srv1.dpetri.net:1026 TIME_WAIT UDP pro1:epmap *:* UDP pro1:microsoft-ds *:* UDP pro1:isakmp *:* UDP pro1:1026 *:* UDP pro1:1027 *:* UDP pro1:1028 *:* UDP pro1:1038 *:* UDP pro1:1043 *:* UDP pro1:1085 *:* UDP pro1:1086 *:* UDP pro1:1242 *:* UDP pro1:ntp *:* UDP pro1:1649 *:* UDP pro1:1900 *:* UDP pro1:2095 *:* UDP pro1:2217 *:* UDP pro1:ntp *:* UDP pro1:1900 *:*
Again, in XP/2003 you can use the -O switch:
C:'WINDOWS>netstat -ao Active Connections Proto Local Address Foreign Address State PID TCP pro1:epmap pro1.dpetri.net:0 LISTENING 860 TCP pro1:microsoft-ds pro1.dpetri.net:0 LISTENING 4 TCP pro1:1025 pro1.dpetri.net:0 LISTENING 908 TCP pro1:1084 pro1.dpetri.net:0 LISTENING 596 TCP pro1:2094 pro1.dpetri.net:0 LISTENING 596 TCP pro1:3389 pro1.dpetri.net:0 LISTENING 908 TCP pro1:5000 pro1.dpetri.net:0 LISTENING 1068 TCP pro1:1084 srv1.dpetri.net:1026 ESTABLISHED 596 TCP pro1:2094 srv1.dpetri.net:1166 ESTABLISHED 596 UDP pro1:epmap *:* 860 UDP pro1:microsoft-ds *:* 4 UDP pro1:isakmp *:* 680 UDP pro1:1026 *:* 1040 UDP pro1:1027 *:* 1040 UDP pro1:1028 *:* 680 UDP pro1:1038 *:* 908 UDP pro1:1043 *:* 624 UDP pro1:1085 *:* 596 UDP pro1:1086 *:* 596 UDP pro1:1242 *:* 1040 UDP pro1:ntp *:* 908 UDP pro1:1649 *:* 596 UDP pro1:1900 *:* 1068 UDP pro1:2095 *:* 976 UDP pro1:2217 *:* 1856 UDP pro1:ntp *:* 908 UDP pro1:1900 *:* 1068



No comments:
Post a Comment